Modernizing Windows Client Management
 |
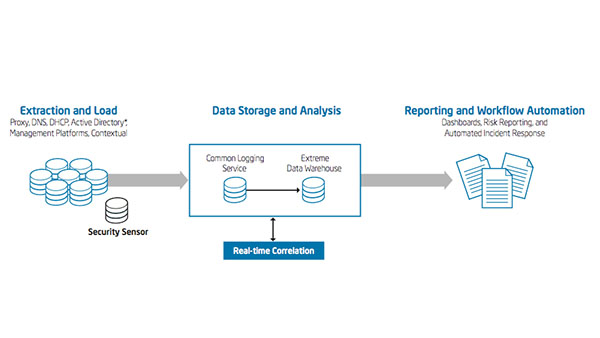
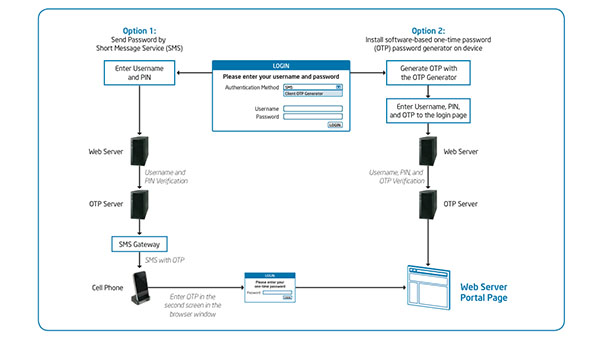
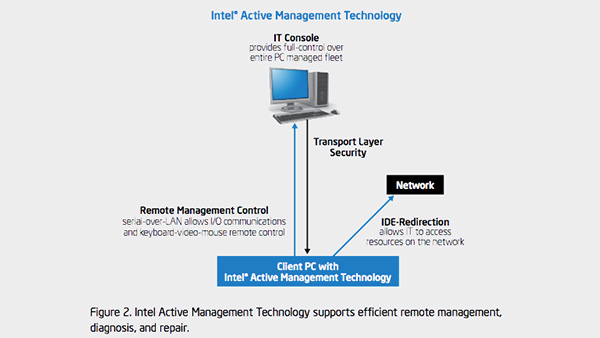
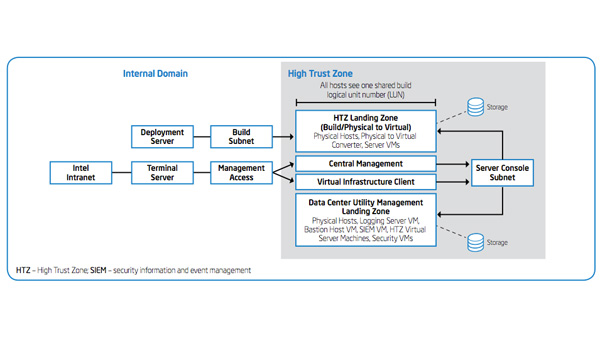
“Why is Intel IT modernizing Windows client management? Because a large part of Intel IT’s job is managing client devices—175,000 end-user and shared PCs for 124,000 employees. We need to consider many factors. Does a PC have the right drivers [See the full post…] |
|
|