 |
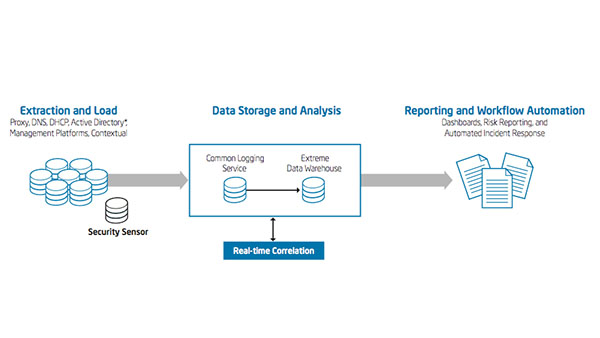
IT Best Practices: Intel IT’s SIEM architecture is based on three layers: common logging service, correlation layer, and predictive analytics. This security BI architecture consumes almost 4 billion events per day to deliver near real-time trends and reporting.
See [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Big Data, cyber security, Enterprise Security, information security, information technology, Insider Threats, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, SEIM
Categories: Big Data, Corporate, HD Video, Information Technology, Intel, Intel IT, IT@Intel, Security, Technology Tags: Alan Ross, Big Data, Cyber Risk Management, cyber security, Enterprise Security, information security, Insider Threats, IT Best Practices, IT@Intel, Security Business Intelligence, SIEM
Categories: Audio Podcast, Inside IT, Intel, Intel IT, IT@Intel, Security Tags: Audio Podcast, B.I., Big Data, Corporate, Cyber Risk Management, Grant Babb, information technology, Inside IT, Insider Threats, Intel, Intel IT, IT Best Practices, IT Business Value, IT infrastructure, IT@Intel, Security


