 |
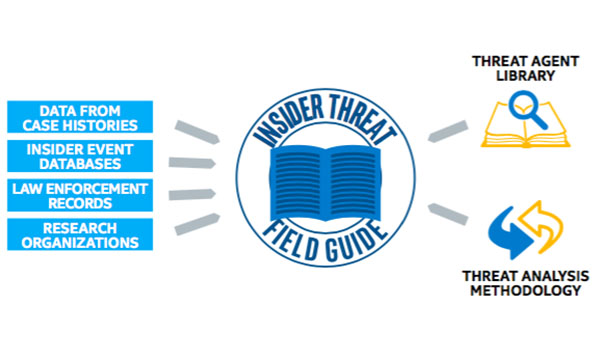
IT Best Practices: One of the most serious security challenges facing enterprises today is that of insider threat. However, many enterprises do not fully understand the scope of the problem and until recently, there has been a lack of [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Enterprise Security, information technology, insider event, insider risk, insider threat agent, Insider threat guide, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, mitigating risk, pdf, threat agent library, Tim Casey
Categories: Cloud Computing, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Ben-Shalom, beyond the edge, cloud, Data Loss Prevention, Dennis Morgan, DLP, Enterprise Security, Eran Birk, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, pdf, SAAS, Security, Shachaf Levi
 |
IT Best Practices: Intel IT’s SIEM architecture is based on three layers: common logging service, correlation layer, and predictive analytics. This security BI architecture consumes almost 4 billion events per day to deliver near real-time trends and reporting.
See [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Big Data, cyber security, Enterprise Security, information security, information technology, Insider Threats, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, SEIM
 |
IT Best Practices: Information security has traditionally revolved around keeping the “good guys” in and the “bad guys” out. Taking a page from the medieval playbook, security professionals have tirelessly built higher virtual walls, deeper digital moats, and more [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, Intel IT Business Review, IT White Papers, IT@Intel Tags: Chris Sellers, Enterprise Security, information technology, Intel, Intel IT, IT Best Practices, IT Business Review, IT Business Value, IT Information Security, IT Whitepaper, IT@Intel, protect to enable
Categories: Business Solutions for IT Managers, Intel, IT White Papers, Security, Technology Tags: Business Solutions for IT Managers, COMGUARD, Enterprise Security, ePO, Intel, Intel Active Management Technology, Intel AMT, IT Best Practices, IT Business Value, IT Whitepaper, McAfee, pdf
 |
IT Best Practices:
Intel IT is replacing our previous software-based encryption solution with McAfee Drive Encryption, an integral component of new McAfee security products such as McAfee Complete Data Protection – Advanced software. This high-performing, reliable solution provides integrated [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Data Protection, encryption, Enterprise Security, Intel IT, Intel Solid-State Drives, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, McAfee Drive Encryption, McAfee ePolicy Orchestrator, SEDs, SSD
 |
IT Best Practices: Intel IT continues to expand and strengthen our bring-your-own-device (BYOD) program offerings. As the variety of devices increases, so does our challenge to maintain security and eDiscovery while protecting employees’ privacy, their data, and the enterprise. [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Android, Big Data, BYOD, Corporate, eDiscovery, Enterprise Security, information technology, innovation, Inside IT, Intel, Intel IT, IT Best Practices, IT Business Value, IT@Intel, Rob Evered, Security
 |
IT Best Practices: Intel IT has completed a pilot of its granular trust model, designed to support key initiatives such as IT consumerization and cloud computing. This trust model provides dynamic security controls and user access to reduce enterprise [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Cloud Computing, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cloud Computing, Enterprise Security, Granular Trust Model, Intel, Intel IT, IT Best Practices, IT Business Value, IT Consumerization, IT@Intel
Categories: Big Data, Corporate, HD Video, Information Technology, Intel, Intel IT, IT@Intel, Security, Technology Tags: Alan Ross, Big Data, Cyber Risk Management, cyber security, Enterprise Security, information security, Insider Threats, IT Best Practices, IT@Intel, Security Business Intelligence, SIEM
Categories: Cloud Computing, data centers, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: business intelligence, CIO, Cloud Computing, consumerization, Enterprise Security, Intel IT, IT annual report, IT Best Practices, IT Business Value, IT@Intel, Kim Stevenson, Social Computing
 |
IT Best Practices: Intel IT is proactively gathering data about Ultrabook devices and how they fit into the enterprise, in anticipation of a wave of new devices and form factors, and the associated expectations from employees who want to [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: business intelligence, Cloud Computing, consumerization, data center efficiency, Deployment, Enterprise Reliability, Enterprise Security, high performance computing, Intel IT, IT Best Practices, IT Business Value, it leadership, IT management, Microsoft Windows 7 Upgrade, mission critical computing, mobile computing, PC upgrade, performance, Remote Support, RISC migration, sustainability, Ultrabooks, virtualization
Categories: HD Video, Intel, Intel IT, IT@Intel, Video Podcast Tags: Cyber Risk Management, Enterprise Security, information security, IntelIT, IT Best Practices, IT@Intel, protect to enable
 |
IT Best Practices: Intel IT created a High Trust Zone (HTZ) architecture to virtualize high-security servers. By identifying and classifying risks, we developed controls to mitigate the risks of moving sensitive information and applications to our private cloud.
[See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Cloud Computing, Cloud Server, Cyber Risk Management, Data Center Solutions, Enterprise Security, High Trust Zone, high-security servers, HTZ, information security, Intel IT, IT Best Practices, IT@Intel, private cloud, virtualization
 |
IT Best Practices: Intel IT finance created a new information security investment model which allows IT management, financial experts and security professionals to analyze and prioritize investments, based on risk mitigation against a variety of security threats. A key [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cyber Risk Management, Enterprise Security, information security, Intel IT, IT Best Practices, IT Investment, IT@Intel, Risk assessment
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: business intelligence, Cloud Computing, Enterprise Security, Intel IT, Intel IT Performance Report, IT Best Practices, IT Business Value, IT Consumerization
Categories: Audio Podcast, Information Technology, Inside IT, Intel, Intel IT, IT@Intel, Security Tags: Cyber Risk Management, Enterprise Security, Inside IT, Intel IT, IT Best Practices, IT Business Value, IT infrastructure, IT@Intel, Malcolm Harkins, Security, security threats
Categories: Cloud Computing, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Cyber Risk Management, Enterprise Security, information security, Intel IT, IT Best Practices, IT Business Value, IT Consumerization
 |
To protect Intel and its customers, Intel IT established a program that assesses, monitors, and enforces the security, privacy, and regulatory compliance of externally facing Intel-branded Web sites and online marketing programs. [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cyber Risk Management, Enterprise Security, information security, Intel IT, IT Best Practices, IT@Intel, Online Marketing Programs
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Microsoft Tags: Client Technology, Cyber Risk Management, Employee Productivity, Enterprise Security, information security, Intel IT, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Business Value, IT Competitive Advantage, IT Continuity, IT efficiency, IT Innovation, IT security, IT@Intel, Windows 7
Categories: Corporate, Healthcare, Information Technology, Intel, Intel IT, Intel vPro, IT@Intel Tags: 3D Animation, Alan Ross, April 1, conficker, Data Protection, Dennis Morgan, e-Discovery, Enterprise Security, Frank Engelman, Healthcare IT, Intel, Intel IT Innovation Centre, IT@Intel, loss prevention, pc security, remote manageability, security use cases, security use models, vPro, worms
 |
Building Confidence In Enterprise Security: What is Your “Blueprint”? – Getting Strategic Using the Security Blueprint (Results of the Participant Survey)
This is Part Four of the second episode of the The “Building Confidence in Enterprise Security” video podcast series, [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Connected Social Media, Corporate, Symantec Tags: Andre Gold, Enterprise Security, Samir Kapuria, Security, Security Blueprint, Symantec
 |
Building Confidence In Enterprise Security: What is Your “Blueprint”? – Getting Strategic Using the Security Blueprint (The Blueprint in Various Industries)
This is Part Three of the second episode of the The “Building Confidence in Enterprise Security” video podcast series, [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Connected Social Media, Corporate, Symantec Tags: Andre Gold, Enterprise Security, risk management, Samir Kapuria, Security, Security Blueprint, Symantec
 |
Building Confidence In Enterprise Security: What is Your “Blueprint”? – Getting Strategic Using the Security Blueprint (Operational and Strategic Elements of the Blueprint)
This is Part Two of the second episode of the The “Building Confidence in Enterprise Security” video [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Connected Social Media, Corporate, Symantec Tags: Andre Gold, Business Continuity, Enterprise Security, Samir Kapuria, Secure Operations, Security, Security Blueprint, Security Organization, Security Strategy, Symantec, Symantec Security Blueprint
 |
Building Confidence In Enterprise Security: What is Your “Blueprint”? – Getting Strategic Using the Security Blueprint.
This is Part One of the second episode of the The “Building Confidence in Enterprise Security” video podcast series, featuring Samir Kapuria and Andre [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Connected Social Media, Corporate, Symantec Tags: Andre Gold, Application Security, data security, Enterprise Security, Samir Kapuria, Security, Security Blueprint, Symantec, System Security
 |
Symantec Group Product Manager Lee Weiner provides an overview of data loss prevention and how companies can work to keep valuable information within their organizations. For more information, visit the Enterprise Security section at:
www.symantec.com [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, Symantec Tags: Enterprise Security, Lee Weiner, Symantec


