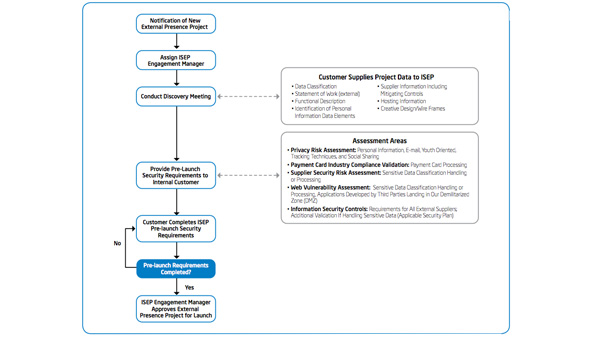
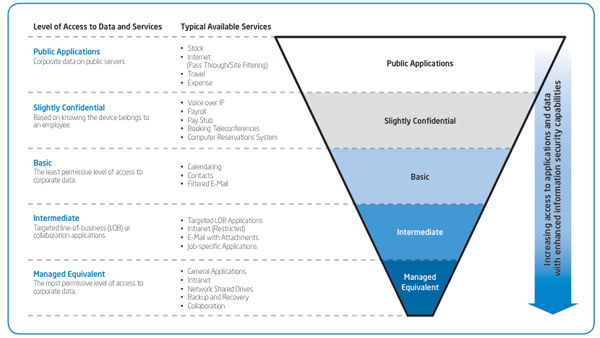
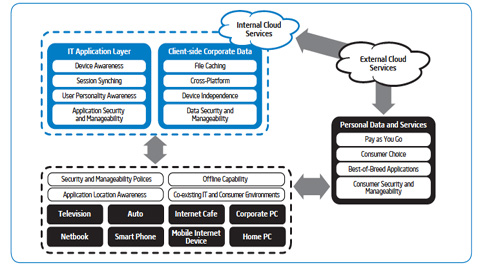
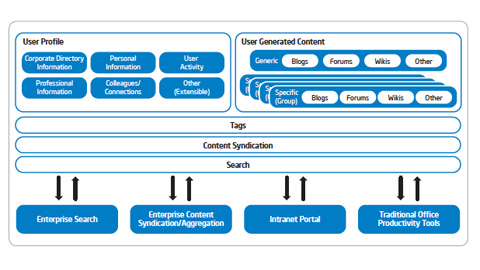
Intel IT Best Practices: PC Fleet Management
 |
Intel IT Best Practices: In this IT@Intel Executive Insights, we explain how Intel IT uses regular refresh, smart technology, the benefits of consumerization and proactive support to help us maintain our PC fleet and empower our 80,000 users across the [See the full post…] |
|
|