Categories: Cloud Computing, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Ben-Shalom, beyond the edge, cloud, Data Loss Prevention, Dennis Morgan, DLP, Enterprise Security, Eran Birk, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, pdf, SAAS, Security, Shachaf Levi
 |
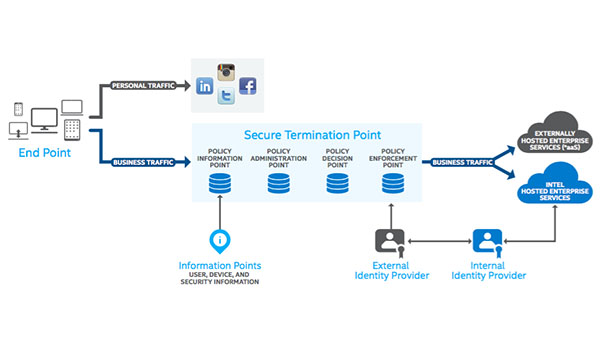
IT Best Practices: To enable rapid adoption of new technologies and usage models—and provide protection in an evolving threat landscape—Intel IT has embarked on a radical five-year redesign of Intel’s information security architecture. [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Alan Ross, Cyber Risk Management, Dennis Morgan, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, Manish Dave, Omer Ben-Shalom, pdf, Security, Stacy Purcell, Tarun Viswanathan, Timothy Verrall, Toby Kohlenberg
Categories: Intel, Intel IT, Intel vPro, IT White Papers, IT@Intel, Security Tags: Alan Ross, Anti-Theft Technology, CMOS, Cyber Risk Management, Dennis Morgan, Disk Encryption, Intel, Intel AT, Intel IT, intellectual property, IT Information Security, IT Whitepaper, IT@Intel, LAN, poison pill, Recovery token, Tarun Viswanathan, Technology Evaluation, Theft Detection, VPN, vPro, WLAN
Categories: Corporate, Healthcare, Information Technology, Intel, Intel IT, Intel vPro, IT@Intel Tags: 3D Animation, Alan Ross, April 1, conficker, Data Protection, Dennis Morgan, e-Discovery, Enterprise Security, Frank Engelman, Healthcare IT, Intel, Intel IT Innovation Centre, IT@Intel, loss prevention, pc security, remote manageability, security use cases, security use models, vPro, worms