 |
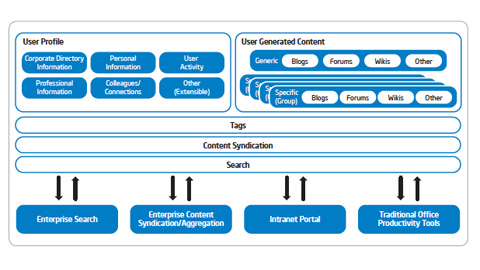
IT Best Practices: Intel IT is implementing an enterprise-wide social computing platform that combines professional networking tools with social media such as wikis and blogs, and integrates with existing enterprise software. Our goal is to transform collaboration across Intel, [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cyber Risk Management, Employee Productivity, green IT, information security, Intel IT, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Business Value, IT Competitive Advantage, IT Continuity, IT efficiency, IT Innovation, IT Sustainabiility, IT@Intel
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cyber Risk Management, Employee Productivity, information security, Intel IT, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Business Value, IT Competitive Advantage, IT Continuity, IT efficiency, IT Innovation, IT@Intel, TARA
 |
IT Best Practices: To minimize the threat posed by malicious software, or malware, making its way into the enterprise, Intel IT has established a process that actively seeks to identify and take action against the malware before it reaches [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Cyber Risk Management, Employee Productivity, information security, Intel IT, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Business Value, IT Competitive Advantage, IT Continuity, IT efficiency, IT Innovation, IT@Intel
 |
IT Innovation: Intel IT developed a new management and support structure for wireless LANs (WLANs). We consolidated first-level support and centralized the WLAN engineer workgroup as well as device management. We manage the WLAN as an integrated service that [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Client Technology, Cyber Risk Management, Employee Productivity, information security, Intel IT, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Business Value, IT Competitive Advantage, IT Continuity, IT efficiency, IT Innovation, IT@Intel
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Client Technology, Cyber Risk Management, Employee Productivity, information security, Intel IT, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Business Value, IT Client Technology, IT Competitive Advantage, IT Continuity, IT efficiency, IT security, IT@Intel
Categories: Intel, Intel IT, Intel vPro, IT White Papers, IT@Intel, Security Tags: Alan Ross, Anti-Theft Technology, CMOS, Cyber Risk Management, Dennis Morgan, Disk Encryption, Intel, Intel AT, Intel IT, intellectual property, IT Information Security, IT Whitepaper, IT@Intel, LAN, poison pill, Recovery token, Tarun Viswanathan, Technology Evaluation, Theft Detection, VPN, vPro, WLAN
Categories: Intel, Intel IT, IT@Intel, Security Tags: Alan Ross, Cyber Risk Management, information technology, Intel IT, IT Information Security, IT security, IT Security Industry, IT Security Management, IT Security Online, IT Security Strategies, IT@Intel, network security
 |
IT Information Security: As our CIO Diane Bryant says “Intel’s success is based on our intellectual property”. To help protect this valuable resource and employees’ personal information, in 2009 Intel IT began deploying full disk encryption on all corporate-owned [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Cyber Risk Management, Employee Productifity, Full Disk Encryption, information security, Intel IT, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Business Value, IT Competitive Advantage, IT Continuity, IT efficiency, IT Information Security, IT@Intel
 |
Security risk assessments, security risk modeling, and protecting against security threats by maintaining a threat agent library — these and other programs form the basis for understanding threats to network security for Intel. In this video podcast, TIm Casey, senior [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Connected Social Media, Corporate, Information Technology, Intel, Intel IT, IT@Intel Tags: Cyber Risk Management, cyber terrorism, hackers, information security, Intel, IntelSecurity, IT Information Security, Matthew Rosenquist, network security, Open Port, Security risk assessments, security risk modeling, security threats, threat agent library, threat agents, Tim Casey, war games
 |
“People are the ultimate threat,” says Tim Casey, a senior strategic analyst for information security at Intel. “People write the viruses, people throw the bombs.” In this interview with PodTech’s Jason Lopez, Casey says that security is all about being [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, Information Technology, InfoWorld, Intel, Intel IT, Intel-OpenPort, IT@Intel Tags: Cyber Risk Management, datacenter, information security, Intel, IntelSecurity, IT Information Security, Jason Lopez, Tim Casey, viruses
 |
Intel Researcher Nina Taft says she was inspired by a newspaper article on how diversity in nature helps organisms thwart the threat of viruses. Her application of principles of biodiversity and her investigation into personalizing security, user by user, could [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, Intel, Security, Technology Tags: biodiversity, Cyber Risk Management, Intel, Jason Lopez, Nina Taft
 |
At RSA 2007 in San Francisco, network security podcaster Martin McKeay headed a series of discussions about the new tools available to consumers, and how far we’ve come. Joining McKeay are Dan Mathews and Brae Legg of Verizon Business. [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Connected Social Media, Corporate, Security, Technology, Verizon Business Tags: Brae Legg, Cyber Risk Management, Dan Mathews, Martin McKeay, RSA 2007, Verizon Business
 |
In a world full of data that is quickly being accessed by mobile devices, ownership over that information — and over one’s own reputation and identity — rises in priority. Searls speaks with Jeremiah Owyang at the recent Mobile Identiy [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Connected Social Media, Security, social media, Tech Conferences and Events, Technology, Web Strategies Tags: Berkman Center, Cyber Risk Management, Jeremiah Owyang, Mobile Identiy Workshop
|
A Symantec Security Response podcast featuring two high-profile zero day vulnerabilities affecting Microsoft and the Broadcom Wireless device driver set. This podcast features a technical discussion of the vulnerabilities and offers listeners insight on likely attack scenarios and mitigating strategies. [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Artificial Intelligence, Connected Social Media, Corporate, Security, Symantec, Technology Tags: Broadcom Wireless, Cyber Risk Management, Dave Cole, Microsoft, Orlando Padilla, Patrick Fitzgerald, Security, Symantec, Symantec Security Response, Zulfikar Ramzan
|
A Symantec Security Response podcast featuring a roundup of the top weblog postings from Symantec Security Response engineers in October. This podcast features a summary of weblogs from Jonathan Omansky, Orla Cox, Candid Wueest and Josh Harriman.
More information at: [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Security, Symantec, Technology Tags: Candid Wueest, Cyber Risk Management, Jonathan Omansky, Josh Harriman, Orla Cox, Security, Symantec
|
A Symantec Security Response podcast focused on a roundup of the latest Symantec Security Response Weblogs for September 2006. The goal of this podcast is to help you better understand some of the threats and trends that Symantec’s Security Response [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, Security, Symantec, Technology Tags: Cyber Risk Management, Symantec, Symantec Security Response
|
A Symantec Security Response podcast focused on the Internet Security Threat Report Volume X and the historical evolution of threats reported by Symantec over the past 4 years. The goal of this podcast is to provide the listener with an [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, Security, Symantec, Technology Tags: Cyber Risk Management, Security, Symantec
|
A Symantec Security Response podcast focused on the Internet Security Threat Report Volume X and Symantec’s predictions on Future Threats. The goal of this podcast is to provide the listener with an overview of the some of the possible threats [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, Security, Symantec, Technology Tags: Cyber Risk Management, Security, Symantec
|
A Symantec Security Response podcast focused on the Internet Security Threat Report Volume X and its key findings. The goal of this podcast is to provide the listener with an overview of the threats and trends covered in Symantec’s latest [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, Security, Symantec, Technology Tags: Cyber Risk Management, Security, Symantec
 |
How do you figure out if legitimate-looking email is attempting to steal your personal information? ShortCuts security expert Rocky Oliver explains how to intercept a phishing attack. This week’s links: Snopes.com, a site for researching and reporting internet hoaxes, [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, IBM, Security, Symantec, Technology Tags: Cyber Risk Management, email, Rocky Oliver, Security
|
A Symantec Security Response podcast focused on the Symantec Home and Home Office Security Report for July 2006. The goal of this podcast is to help you better understand some of the threats and trends identified in the report and [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, Security, Symantec, Technology Tags: Cyber Risk Management, Home Office, Security, Symantec


