Getting Ahead of Malware
October 7th, 2010 |
Connected Social Media Syndication
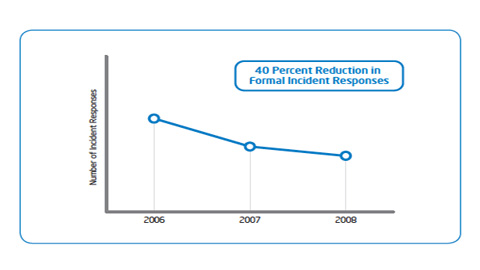
IT Best Practices: To minimize the threat posed by malicious software, or malware, making its way into the enterprise, Intel IT has established a process that actively seeks to identify and take action against the malware before it reaches Intel’s user base. This process focuses on real-time monitoring and interpretation of security events on the network and taking immediate action against any identified threats.
For more on Information Security, see Intel.com/IT
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security

