 |
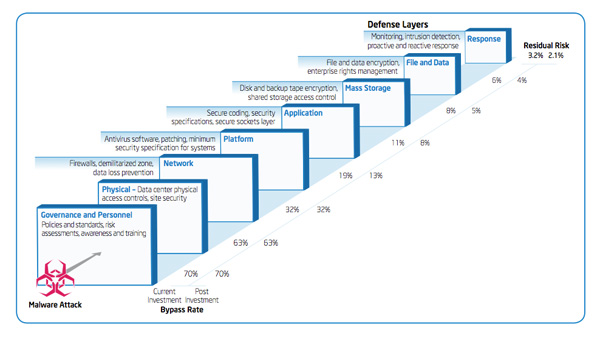
IT Best Practices: Intel IT finance created a new information security investment model which allows IT management, financial experts and security professionals to analyze and prioritize investments, based on risk mitigation against a variety of security threats. A key [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cyber Risk Management, Enterprise Security, information security, Intel IT, IT Best Practices, IT Investment, IT@Intel, Risk assessment
Categories: Audio Podcast, Information Technology, Inside IT, Intel, Intel IT, IT@Intel, Security Tags: Cyber Risk Management, Enterprise Security, Inside IT, Intel IT, IT Best Practices, IT Business Value, IT infrastructure, IT@Intel, Malcolm Harkins, Security, security threats
 |
IT Best Practices: To enable rapid adoption of new technologies and usage models—and provide protection in an evolving threat landscape—Intel IT has embarked on a radical five-year redesign of Intel’s information security architecture. [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Alan Ross, Cyber Risk Management, Dennis Morgan, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, Manish Dave, Omer Ben-Shalom, pdf, Security, Stacy Purcell, Tarun Viswanathan, Timothy Verrall, Toby Kohlenberg
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Christmas, Cyber Risk Management, Cybercriminals, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, IT@Intel Technology Tips, Scams, Security, theft, X-Mas, Xmas
Categories: Audio Podcast, Cloud Computing, Intel Conversations in the Cloud, Security, VMware Tags: Allyson Klein, applications, Cloud Computing, Conversations in the Cloud, Cyber Risk Management, data center, Intel, manageability, reliability, Security, server, Stu Miniman, VMworld, Wikibon
Categories: Audio Podcast, Information Technology, Inside IT, Intel, Intel IT, IT@Intel, Security Tags: 9/11, Brad Ellison, Business Continuity, cyber attacks, Cyber Risk Management, data security, disaster preparedness, FEMA, Inside IT, Intel IT, IT Best Practices, IT Business Value, IT infrastructure, IT@Intel
 |
IT Best Practices: Episode 5 – The IT organization is undergoing rapid change. Changes like virtualization and consumerization present new opportunities for business, and new challenges for IT. Cloud computing shifts IT to more of a creator and distributor [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Audio Podcast, Cloud Computing, Inside IT, Intel, Intel IT, IT@Intel, Security Tags: Alan Ross, Cyber Risk Management, Inside IT, Intel IT, IT Best Practices, IT Business Value, IT Cloud Computing, IT infrastructure, IT@Intel, mobility, Security, virtualization
 |
IT Best Practices: Intel chose to encrypt all corporate notebooks to keep data from being accessed if lost or stolen. Including a detailed plan for secure and cost-effective implementation, Intel IT combined a software and hardware based solution to [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Cyber Risk Management, encryption, Intel IT, IT Best Practices, IT Business Value, IT security, IT@Intel, mobile security, mobility
 |
IT Best Practices: Intel IT security specialists deployed PCs with Intel vPro technology, focusing on high-priority areas including investigations, data protection, and loss prevention and system health. Testing and validating these capabilities, Intel was able to deliver reduced manual [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Core vPro, Cyber Risk Management, Data Protection, drive encryption, encryption, full disk, hard disk encryption, Healthcare IT, Intel IT, IT Best Practices, IT Business Value, IT security, IT@Intel, laptop, mobility, notebook, pilot, privacy, proof of concept, protect data, Security, stolen notebook, stolen pc, theft, vPro
 |
IT Best Practices: The IT@Intel program connects IT professionals around the world with their IT peers inside our organization – sharing lessons learned, methods and strategies. Our goal is simple: Share the Intel IT best practices that create business [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: business, business intelligence, collaboration, Cyber Risk Management, data center, employee, financial valuation, information security, Intel IT, IT Best Practices, IT Business Value, IT Competitive Advantage, IT Sustainability, IT@Intel, productivity, Server Refresh, social media, strategic planning, sustainability
 |
In this episode of The Tomorrow Project: Brian David Johnson, Futurist at Intel Corporation, interviews Tadayoshi Kohno about embedded computational devices and security.
Kohno, a scientist and researcher at the University of Washington, studies how everyday devices around us [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: HD Video, Intel, Security, The Tomorrow Project, Video Podcast Tags: Brian David Johnson, Car Security, Car Technology, Cyber Risk Management, Futurist, Intel, Medical Security, Medical Technology, Medicine, Tadayoshi Kohno, The Tomorrow Project, University of Washington
Categories: Cloud Computing, HD Video, Information Technology, Intel, Intel IT, IT@Intel, Security, Technology, Video Podcast Tags: Cloud Computing, Cyber Risk Management, information security, Intel IT, IT Best Practices, IT Business Value, Malcolm Harkins
Categories: Information Technology, Intel, Intel IT, IT@Intel, Research@Intel, Security, social media, Video Podcast Tags: Cyber Risk Management, information security, Intel IT, IT Best Practices, IT Business Value, IT@Intel, Malcolm Harkins, Social Computing, social media, Technology
Categories: Cloud Computing, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Cyber Risk Management, Enterprise Security, information security, Intel IT, IT Best Practices, IT Business Value, IT Consumerization
Categories: Corporate, HD Video, Information Technology, Intel, Intel IT, IT@Intel, Security Tags: CISO, Cyber Risk Management, information security, Intel IT, IT Best Practices, IT Business Value, IT@Intel, Malcolm Harkins
Categories: HD Video, Information Technology, Intel, Intel IT, IT@Intel, Security Tags: CISO, Cyber Risk Management, Enterprise Security management, information security, Intel IT, IT Best Practices, IT Business Value, Malcolm Harkins
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cyber Risk Management, Employee Productivity, information security, Intel IT, IT Best Practices, IT Business Value, IT@Intel
 |
To protect Intel and its customers, Intel IT established a program that assesses, monitors, and enforces the security, privacy, and regulatory compliance of externally facing Intel-branded Web sites and online marketing programs. [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cyber Risk Management, Enterprise Security, information security, Intel IT, IT Best Practices, IT@Intel, Online Marketing Programs
Categories: Cloud Computing, Intel, Intel Chip Chat, Security Tags: AES-NI, Allyson Klein, Cloud Computing, Cyber Risk Management, Dylan Larson, encryption, Intel, Intel Chip Chat, Xeon
Categories: Audio Podcast, Information Technology, Inside IT, Intel, Intel IT, IT@Intel Tags: Alan Ross, Cyber Risk Management, information security, Inside IT, Intel IT, IT Best Practices, IT Business Value, IT@Intel, Malcolm Harkins, Security
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Microsoft Tags: Client Technology, Cyber Risk Management, Employee Productivity, Enterprise Security, information security, Intel IT, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Business Value, IT Competitive Advantage, IT Continuity, IT efficiency, IT Innovation, IT security, IT@Intel, Windows 7
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Client Technology, Cloud Computing, Cyber Risk Management, data center, Employee Productivity, green IT, information security, Intel IT, Intel IT Performance Report, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Business Value, IT Competitive Advantage, IT Continuity, IT efficiency, IT Innovation, IT Sustainability, IT@Intel
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cyber Risk Management, Employee Productivity, information security, Intel, Intel IT, IT Best Practices, IT security, IT@Intel
Categories: Information Technology, Intel, Intel IT, IT@Intel, Security Tags: Cyber Risk Management, encryption, Intel, Intel Active Management Technology, Intel IT, IT Best Practices, IT Business Value, IT security, IT@Intel, Matt Bodin, Passwords
 |
IT Best Practices: To enable device-independent mobility (DIM) at Intel, Intel IT is considering implementing dynamic virtual client (DVC) technology, which uses containerized software appliances to abstract the OS; applications; corporate and personal data and workspaces; and user-specific settings. [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Cloud Computing, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Client Technology, Cyber Risk Management, Employee Productivity, information security, Intel IT, IT Best Practices, IT Business Agility, IT Business Efficiency, IT Cloud Computing, IT Competitive Advantage, IT Continuity, IT efficiency, IT@Intel


