IT Best Practices: The Relevance of Desktop Computing in a Mobile Enterprise
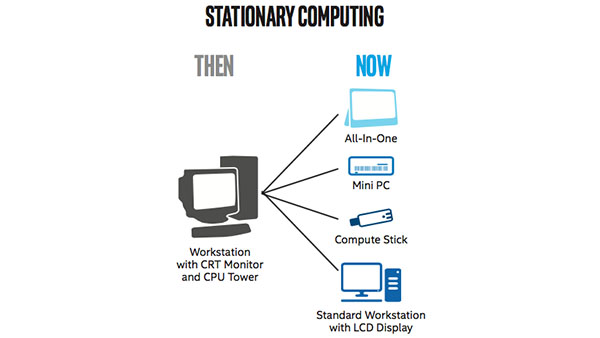
IT Best Practices: While Intel’s PC fleet consists primarily of Intel architecture-based mobile devices, such as business Ultrabook devices, tablets, and a growing number of 2-in-1 devices, familiar desktop-class PCs continue to fill an important role. In fact these PCs are evolving and expanding their relevance in the workplace. Intel IT studies have repeatedly shown that a single device type does not meet the needs of all Intel employees. We believe it is important to offer multiple technology choices, enabling employees to select the best device for their jobs and ways of working.
Historically, desktop-class computing in the enterprise has been defined as a workstation-type PC with a high-performance CPU and one or more monitors. With advances in technology, Intel IT is expanding the role of desktop-class computing beyond the desk. With new form factors, such as mini PCs, all-in-one PCs, and compute sticks, stationary computing devices (also referred to as simply “desktops”) in the enterprise can be used in a variety of settings.
We have identified individual, public, and shared use cases for enterprise-level stationary computing devices. In all these use cases, we protect our assets by taking advantage of the remote management and security features of Intel architecture and the Intel Security software stack. Examples of these features include Intel vPro technology, Intel Solid-State Drive Pro 2500 Series, McAfee ePolicy Orchestrator, and anti-malware and host intrusion prevention software. As the integrated hardware and software suite advances with new generations of Intel processors, we plan to investigate new hardware-enhanced security features.
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Information Technology, Intel, Intel IT, IT White Papers, IT@Intel

