 |
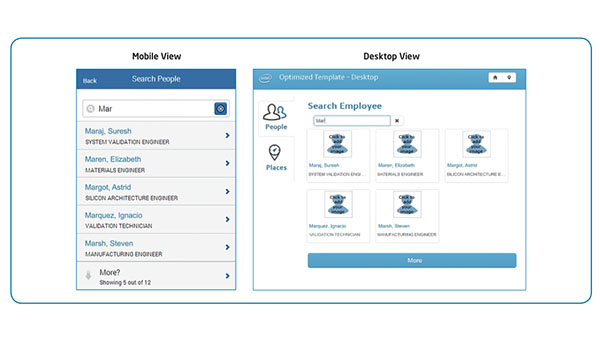
IT Best Practices: Intel IT has implemented a new type of software architecture that enables us to develop large-scale, UI-optimized, cross-platform applications using a single code base with maximum code reuse between supported platforms.
With the consumerization of IT [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cross-Platform Apps, developer experience, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, Mark Reidman, mobile app development, Model View ViewModel, MVVM, Object-oriented programming, OOP, Samion Kuptiev, user experience
Categories: Audio Podcast, Big Data, Information Technology, Inside IT, Intel, Intel IT, IT@Intel Tags: Apache, Audio Podcast, BI, Big Data, business intelligence, Chandu Yalla, Corporate, Hadoop, information technology, innovation, Inside IT, Intel, Intel IT, IT Best Practices, IT Business Value, IT@Intel
Categories: Audio Podcast, Information Technology, Inside IT, Intel, Intel IT, IT@Intel, Security Tags: Audio Podcast, Corporate, design, Elaine Rainbolt, information technology, innovation, Inside IT, Intel, Intel IT, IT Best Practices, IT Business Value, IT@Intel, Malcolm Harkins, Roland Cloutier, RSA, RSA Security Conference, Security, Security by Design
 |
IT Best Practices: Episode 70 – Over the last decade, Intel IT has been employing virtualization technology in the data center for the office, enterprise, and service environments. Servers have been virtualized, and server and storage provisioning have become [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Audio Podcast, Corporate, data centers, Information Technology, Inside IT, Intel, Intel IT, IT@Intel Tags: Audio Podcast, cloud strategy, Corporate, data center, information technology, innovation, Inside IT, Intel, Intel IT, IT Best Practices, IT Business Review, IT Business Value, IT@Intel, SDN, Software Defined Networking, Sridhar Mahankali, virtualization
 |
IT Business Value: We use three key metrics to measure data center transformation success: meet growing customer demand (service-level agreements and quality of service) within constrained spending targets (cost-competitiveness) while optimally increasing the utilization of infrastructure assets (operational efficiency). [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Data Center Strategy, DC Refresh, DOMES, Intel, Intel IT, IT Best Practices, IT Business Value, IT@Intel, NUMA-Booster, Shesha Krishnapura
 |
IT Best Practices: As Intel’s bring-your-own-device (BYOD) program grows and Android devices become more popular, Intel IT wants to help employees using these devices while also keeping the enterprise secure. We are delivering a native email solution that enables [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Aideen Prendergast, Android, Android devices, Android Security, Derek Harkin, Emer Roche, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT White Paper, IT Whitepaper, IT@Intel, mobile device management, mobile security, native email solution, Paul Donohue, pdf, Rob Evered, secure container
 |
IT Best Practices: Intel IT and Corporate Services, working as a team, have identified a range of factors to consider when choosing a data center site. When Intel experiences growth that requires investment in data center facilities, the project [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, data centers, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Data Center Site Selection, Ed Austin, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, Jeff Lee, John Musilli, Marissa Mena, Paul Vaccaro, pdf
Categories: Audio Podcast, Corporate, data centers, Information Technology, Inside IT, Intel, Intel IT, IT@Intel Tags: Audio Podcast, Corporate, data center, information technology, innovation, Inside IT, Intel, Intel IT, Intel IT Performance Report, IT Best Practices, IT Business Review, IT Business Value, IT@Intel, Server Refresh, Shesha Krishnapura, Xeon E7-4800 v2
 |
IT Best Practices: Teamwork starts with listening. Listening leads to understanding. Understanding fosters alignment and informed activity.
What sounds so simple and so fundamental isn’t always the norm. Often overwhelmed with new service requests, systems administration, infrastructure optimization, and [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, Intel IT Business Review, IT White Papers, IT@Intel Tags: Ed Goldman, Faith McCreary, information technology, Intel, Intel IT, Intel IT Business Review, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, Mac Agan
 |
IT Best Practices: Creating new products. Accelerating time to market. Expanding and evolving a world-wide design organization.
Supporting these efforts is hard enough. Driving them forward is even harder.
Some 20 years ago, the product design team at Intel [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, Intel IT Business Review, IT White Papers, IT@Intel Tags: Dan McKeon, information technology, Intel, Intel IT, Intel IT Business Review, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, product design, Product Development IT
 |
IT Best Practices: Information security has traditionally revolved around keeping the “good guys” in and the “bad guys” out. Taking a page from the medieval playbook, security professionals have tirelessly built higher virtual walls, deeper digital moats, and more [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, Intel IT Business Review, IT White Papers, IT@Intel Tags: Chris Sellers, Enterprise Security, information technology, Intel, Intel IT, IT Best Practices, IT Business Review, IT Business Value, IT Information Security, IT Whitepaper, IT@Intel, protect to enable
 |
IT Best Practices: Imagine a security poverty line… below this line are individuals or organizations who do not have the skills, resources or funding to protect, detect and respond to cybersecurity threats. Many organizations and individuals fall below this [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Featured, HD Video, Intel, Intel IT, IT@Intel, Security, Video Podcast Tags: information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT security, IT Whitepaper, IT@Intel, Malcolm Harkins
Categories: Audio Podcast, Cloud Computing, Information Technology, Inside IT, Intel, Intel IT, IT@Intel Tags: Audio Podcast, BI, Big Data, business intelligence, cloud, Cloud BI, Corporate, information technology, innovation, Inside IT, Intel, Intel IT, Intel IT Performance Report, IT Best Practices, IT Business Review, IT Business Value, IT@Intel, mobile, mobility, Yatish Goel
Categories: Corporate, Featured, HD Video, Information Technology, Intel, Intel IT, IT@Intel, Video Podcast Tags: context aware, future, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Labs, IT Whitepaper, IT@Intel, mobility, pdf, sensors, Vision, Wearables
 |
IT Best Practices: Over the past two years, Intel IT has validated and improved its mobile application development framework, Focusing first on native development, we identified best-known methods (BKMs) that we used to refine our framework and applied these [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Intel, Intel IT, IT White Papers, IT@Intel Tags: David Byrne, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, Joseph Doolittle, mobile app development, mobile enterprise applications, Patrick Salo, pdf
 |
IT Best Practices: Intel IT believes that the combination of powerful Intel architecture-based tablets and Microsoft Windows 8 provides significant productivity benefits to employees, as well as improved manageability and information security capabilities. This paper describes our process and [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Corporate, Featured, HD Video, Information Technology, Intel, Intel IT, IT@Intel, Technology, Video Podcast Tags: information technology, Intel, Intel architecture-based tablets, Intel IT, IT Best Practices, IT Business Value, IT video, IT Whitepaper, IT@Intel, John Mahvi, tablets, Tiffany Pany, Windows 8, Windows 8 deployment
 |
In 2013 Intel IT set a target to reduce all reported IT incidents requiring our attention by 40 percent by the end of the year. We devised a client incident prediction Proof of Concept (PoC) using Intel Distribution for Apache [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Ajay Chandramouly, Asoka Diggs, Big Data, Guillermo Rueda, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, predictive analytics, Ravindra Narkhede, Vijay Mungara
 |
IT Best Practices: Episode 66 – Technological advances in our connected world are pressing businesses to re-examine privacy policies everywhere. That’s certainly true at Intel, where Stuart Tyler is a Senior Privacy Analyst in the Intel Security and Privacy [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Audio Podcast, Information Technology, Inside IT, Intel, Intel IT, IT@Intel, Security Tags: Audio Podcast, Corporate, information technology, innovation, Inside IT, Intel, Intel IT, IT Best Practices, IT Business Value, IT@Intel, principles, privacy, Security, Stuart Tyler
Categories: Audio Podcast, data centers, Information Technology, Inside IT, Intel, Intel IT, IT@Intel Tags: Audio Podcast, Corporate, data center, information technology, innovation, Inside IT, Intel, Intel IT, IT Best Practices, IT Business Value, IT@Intel, Shesha Krishnapura
 |
IT Best Practices: People are the Perimeter – In today’s mobile world, people are the new security perimeter. Organizations and companies, including their products, customers and employees, are exposed to increasing security threats – both in number and complexity. [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Featured, HD Video, Intel, Intel IT, IT@Intel, Security, Video Podcast Tags: data security, information security, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, pdf, privacy, privacy principles, protect to enable, Security
 |
IT Best Practices: In IT, the technical strategy and architecture group is responsible for driving the enterprise capabilities to support our efforts. This year, we are concentrating much of our energy towards the implementation of what we call five-star [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Intel, Intel IT, IT White Papers, IT@Intel Tags: CTO, Ed Goldman, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, Multi-Platform Apps, pdf
 |
IT Best Practices: While Intel IT has routinely received high marks for performance, I believe we can do more. I believe we can help transform the business in significant and impactful ways. This requires new thinking, new strategies, and [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Brian Sutton:, Changing the IT Leader’s Mindset, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, Kim Stevenson, pdf, Robina Chatham
Categories: Audio Podcast, Information Technology, Inside IT, Intel, Intel IT, IT@Intel Tags: Audio Podcast, BI, Big Data, business intelligence, Corporate, Data Visualization, David Schaefer, information technology, innovation, Inside IT, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, pdf, self-service BI
Categories: Corporate, Featured, HD Video, Information Technology, Intel, Intel IT, IT@Intel, Security, Video Podcast Tags: data security, information security, information technology, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, Malcolm Harkins, privacy, privacy principles, protect to enable
 |
IT Best Practices:
Intel IT is replacing our previous software-based encryption solution with McAfee Drive Encryption, an integral component of new McAfee security products such as McAfee Complete Data Protection – Advanced software. This high-performing, reliable solution provides integrated [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security Tags: Data Protection, encryption, Enterprise Security, Intel IT, Intel Solid-State Drives, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, McAfee Drive Encryption, McAfee ePolicy Orchestrator, SEDs, SSD


