Enabling NFV to Deliver on its Promise
 |
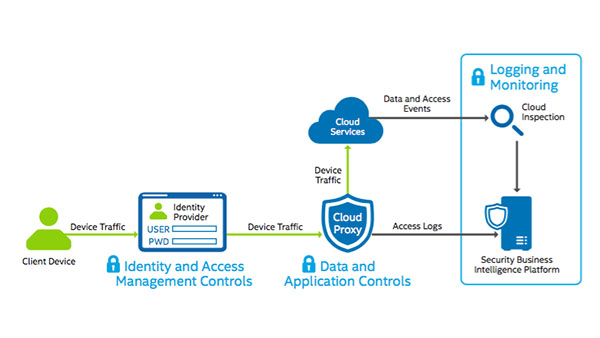
Software Defined Infrastructure: Network functions virtualization (NFV) is paving the way for more open, exible, and economical networking and communications equipment based on general-purpose computing platforms instead of traditional proprietary, purpose-built products. However, this transition hinges on increasing performance and [See the full post…] |
|
|