SaaS Security: Best Practices for Minimizing Risk
IT Best Practices: To support Intel business groups’ increasing demand for software-as-a-service (SaaS) applications, Intel IT has developed several best practices that can help enhance SaaS security and protect Intel’s intellectual property.
SaaS applications can provide efficiency and agility, cost savings, and enhanced collaboration especially with suppliers and customers. At the same time, SaaS applications present security challenges because they are hosted on third-party infrastructure and run third-party application code.
We have established the following best practices to minimize risk in the cloud:
• Develop a SaaS security strategy and build a SaaS security reference architecture that reflects that strategy.
• Balance risk and productivity.
• Implement SaaS security controls.
• Keep up with technology development.
In our experience, SaaS security controls fall into the following categories:
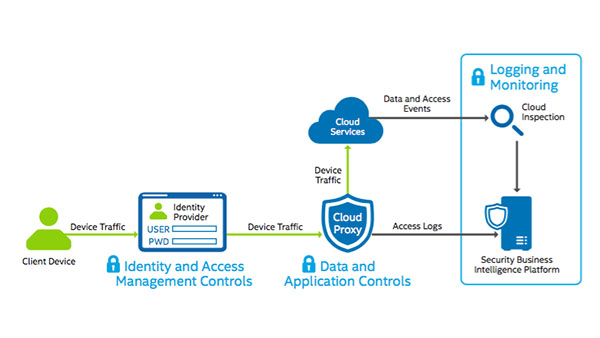
• Identity and access management controls. These controls help ensure that SaaS applications are accessed by the appropriate users and only from approved devices.
• Application and data controls. As an interface to data, applications must be registered and evaluated to determine whether they meet security requirements. Data encryption, tokenization, and data loss prevention (DLP) techniques protect data and help detect storage or transmission of sensitive information in ways that do not comply with information security policy. Data controls can be applied in real-time to cloud traffic, or to content that is already stored in the cloud.
• Logging and monitoring controls. These controls help us detect information security violations, send alerts to the appropriate IT staff, initiate appropriate responses, and correct the situation< Our SaaS security best practices enhance security, privacy, and legal compliance at Intel. They also make it possible for business groups to quickly adopt new SaaS solutions.
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Intel, Intel IT, IT White Papers, IT@Intel

