Evolving the Mobile Employee Hotspot for IT Consumerization
IT Best Practices: IT consumerization and the business need for broader network access present Intel IT with a continuously evolving challenge. The growing adoption of bring your own device (BYOD) poses additional challenges as consumer choices expand and employee expectations for network support grows.
In 2005, Intel IT implemented a Guest Internet Access Wi-Fi network, giving contractors and visitors on Intel’s campuses the ability to access the Internet using their own devices for business reasons. In late 2007 the mobile industry was transformed with the first touch smartphones. By 2009 many employees had smartphones, but they could not use them to connect to the enterprise Wi-Fi network. In 2010, Intel IT enabled a mobile Employee Hotspot service to accommodate personal devices accessing the Internet. But what began as a benefit for employees has provided significant value to the business, increasing employee productivity.
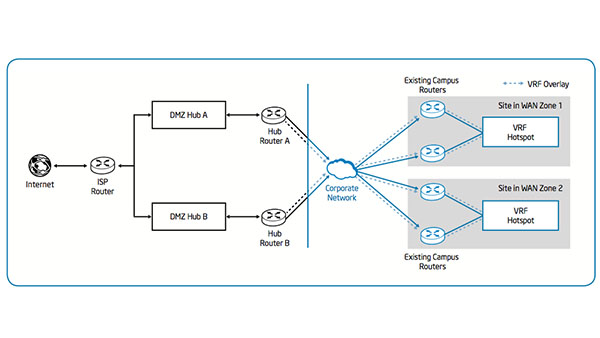
We anticipate multiple devices per employee in the future and advances in device technology that will require more bandwidth and connectivity options. To stay ahead of demand, we re-architected the overall Employee Hotspot service using an overlay network, making it easier to deploy with lower cost. This new overlay network uses virtual routing and forwarding technology, which can use our existing network infrastructure without additional hardware.
Benefits: Better security, scalability, usability, and productivity—and lower costs.
Posted in:
Information Technology, Intel, IT White Papers, IT@Intel, Security

