Let’s Talk IT: What is vPro
 |
Let’s Talk IT: In this episode host Michele Gartner chats with Richard Foote about vPro, and she gets a demo from Minh Pham who does a remote search and destroy of a virus on a client PC. |
|
|
 |
Let’s Talk IT: In this episode host Michele Gartner chats with Richard Foote about vPro, and she gets a demo from Minh Pham who does a remote search and destroy of a virus on a client PC. |
|
|
 |
IT Best Practices: Episode 47 – Intel has implemented a new granular trust model to improve security throughout the enterprise. It’s designed to support key initiatives like IT consumerization and cloud computing. At the same time Intel wants to keep [See the full post…] |
|
|
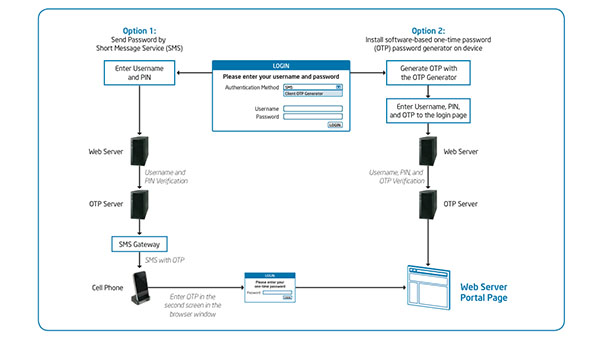 |
IT Best Practices: To make it easier for employees to use small form factor devices to accomplish job duties, Intel IT is developing an enhanced connectivity solution. This solution will help broaden the range of applications available to managed devices [See the full post…] |
|
|
 |
IT Best Practices: Episode 46 – IT has developed a new partnership with its users over the past few years. Changes in technology, and the needs and demands of employees, have created new flexibility and greater choice for workers. Intel [See the full post…] |
|
|
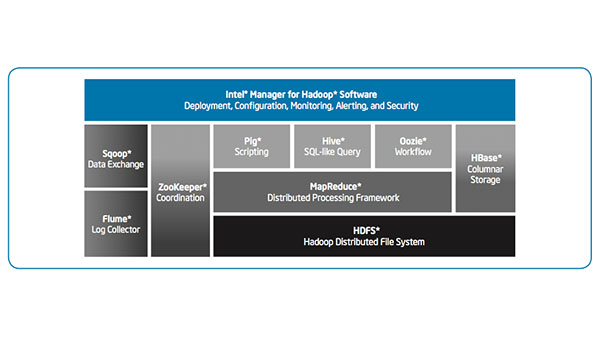 |
IT Best Practices: Intel IT compared the Intel Distribution for Apache Hadoop software (Intel Distribution) to two other Apache Hadoop distributions using a well-defined set of evaluation criteria. The evaluation criteria included aspects of platform architecture; administration, operations, and support; [See the full post…] |
|
|
 |
IT Best Practices: As velocity and complexity of Intel’s business accelerates, Intel IT has identified explosive opportunities for business intelligence — especially advanced analytics — to become a significant competitive differentiator for Intel. Intel IT, working with internal business groups, [See the full post…] |
|
|
 |
IT Best Practices: Episode 45 – Intel’s approach to security has evolved. The current strategy looks to apply reasonable protections that allow information to flow through the organization. This reduces risk, but maintains a quality user experience. A big component [See the full post…] |
|
|
 |
IT Business Value: Learn about Intel IT’s strategies and initiatives that are accelerating Intel’s business growth in the 2012-13 Intel IT Annual Performance Report. Learn how Intel IT is delivering business value through big data, cloud computing, consumerization of IT, [See the full post…] |
|
|
 |
IT Best Practices: Episode 43 – There’s a revolution going on in workplace computing at Intel. In previous podcasts we’ve talked about the introduction of new, portable platforms, the bring-your-own-device program, and the deployment of Windows 8 throughout the enterprise. [See the full post…] |
|
|
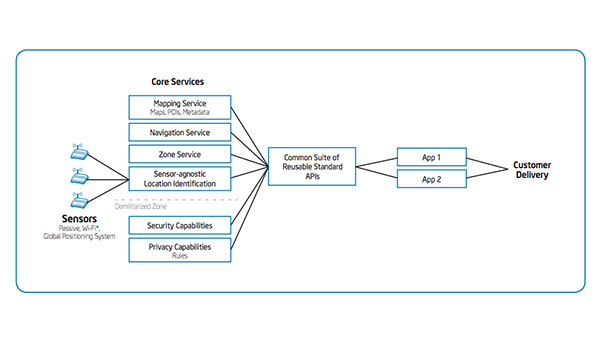 |
IT Best Practices: Intel IT recognizes a great opportunity for the use of location-based services in the enterprise, and we are already piloting three location-based applications: FriendFinder, WayFinder, and You Are Here mapping that use location-based services. Employees can choose [See the full post…] |
|
|
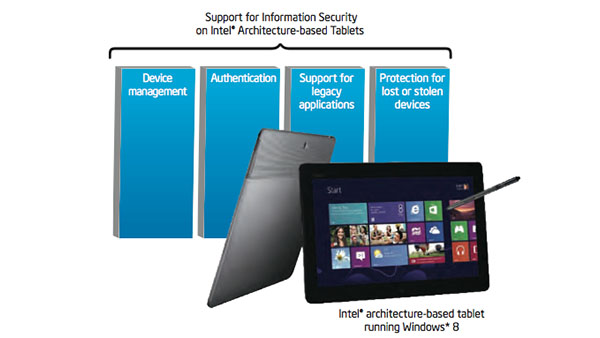 |
IT Best Practices: Intel IT is currently evaluating the information security and privacy protection features of Intel architecture-based tablets running Windows 8 Enterprise. Our initial evaluations indicate that, together, Windows 8 and Intel architecture provide a compelling platform for mobile [See the full post…] |
|
|
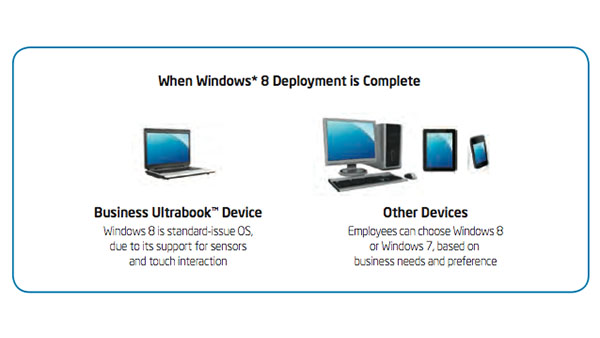 |
IT Best Practices: Intel IT is standardizing on Windows 8 as the primary operating system for business Ultrabook devices and Intel architecture-based tablets. We are accelerating the deployment readiness for business Ultrabook devices and tablets, and intend to make the [See the full post…] |
|
|
 |
IT Best Practices: As Intel IT builds cloud infrastructure and enables cloud services, one of the goals is to make those services available to as broad a range of devices as possible. To do so, we are integrating our cloud [See the full post…] |
|
|
 |
IT Best Practices: Intel IT is proactively implementing a bring-your-own-device (BYOD) program that allows employees the flexibility to use personally owned devices like smartphones and tablets to connect to the corporate network for some IT services. While this presents productivity [See the full post…] |
|
|
 |
IT Best Practices: Episode 42 – Big changes are coming to the Intel workplace this year. In our last podcast we talked about the company’s Ultrabook rollout that’s taking place in 2013, expected to bring thousands of new devices to [See the full post…] |
|
|
 |
IT Best Practices: Intel IT is exploring data anonymization—the process of obscuring published data to prevent the identification of key information—in support of our vision of a hybrid cloud computing model and our need to protect the privacy of our [See the full post…] |
|
|
 |
IT Best Practices: Intel IT is implementing platform as a service (PaaS) to accelerate custom application deployment and promote cloud-aware application design. Our traditional application deployment process is less-than-ideal, taking as much as 140 days to deploy a new application. [See the full post…] |
|
|
 |
IT Best Practices: Episode 41 – The look of the modern workplace is changing all the time. The way people worked five years ago is significantly different from the way they work now, which in turn will be substantially different [See the full post…] |
|
|
 |
IT Best Practices: Find out what happens when Carl carelessly shares his sensitive information on “Friend Party”. Intel and McAfee partner to show how trusting strangers can turn something fun and useful into a huge problem. Learn more at mcafee.com/advice. |
|
|
 |
IT Best Practices: Episode 40 – The role of a corporate web site has evolved. It’s no longer just a static source of information. It’s the place where a company creates and maintains a relationship with the world of customers, [See the full post…] |
|
|
 |
IT Best Practices: Episode 39 – You could say that Business Intelligence is the collective knowledge of an enterprise. How intelligent a particular business is depends on a lot of factors, but the ability to make sense of a vast [See the full post…] |
|
|
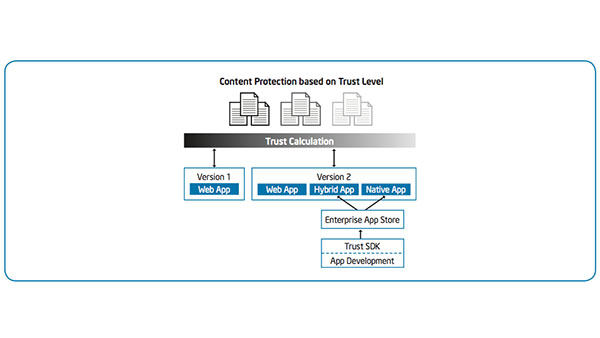 |
IT Best Practices: Intel IT has completed a pilot of its granular trust model, designed to support key initiatives such as IT consumerization and cloud computing. This trust model provides dynamic security controls and user access to reduce enterprise risk [See the full post…] |
|
|
 |
IT Best Practices: Episode 38 – More and more, Intel is offering consumer-facing web services, like the AppUp store. That creates new challenges – consumers expect web services to be always available, and demand for services can spike or drop [See the full post…] |
|
|
 |
Intelligent Storage: How Jaguar Land Rover made the best use of big data and HPC to design the award-winning Evoque. Manufacturing customers are turning to Intel technologies to make more efficient use of big data for high-performance computing, analysis, and [See the full post…] |
|
|
 |
IT Best Practices: Episode 37 – Consumerization is a big trend in the enterprise. Intel is at the forefront of this trend, with an extensive BYO program. Tens of thousands of employee-owned smart phones and tablets are now in use [See the full post…] |
|
|