IT Best Practices: Rethinking Information Security to Improve Business Agility
 |
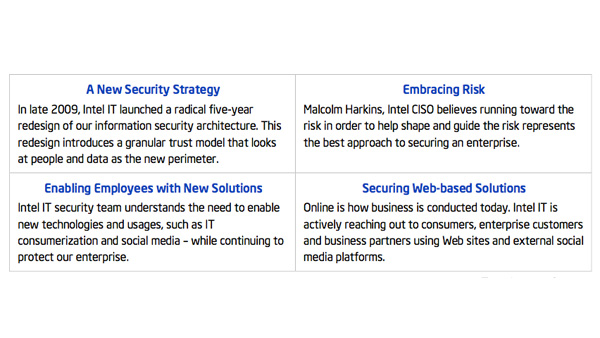
IT Best Practices: To enable rapid adoption of new technologies and usage models—and provide protection in an evolving threat landscape—Intel IT has embarked on a radical five-year redesign of Intel’s information security architecture. |
|
|