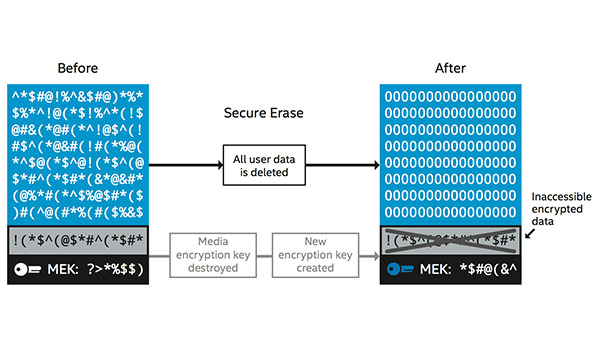
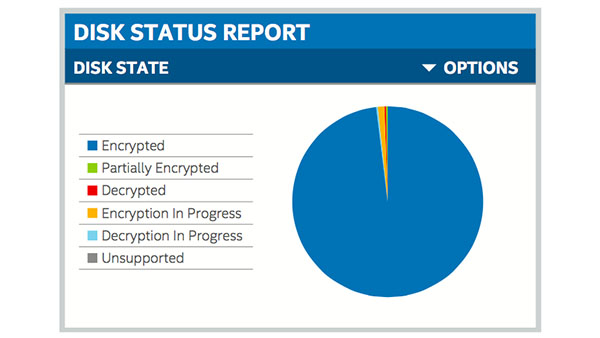
Network Security Platforms – Intel Chip Chat: Network Insights – Episode 117
 |
Intel Chip Chat – Network Insights audio podcast with Allyson Klein: Sven Freudenfeld, Director Global Business Development at Lanner Electronics Inc., examines the landscape of network security through the lens of network transformation. He discusses where customers are in terms [See the full post…] |
|
|