Deploying Intel Solid-State Drives with Managed Hardware-Based Encryption
IT Best Practices: To gain the security benefits of centrally managed hardware-based encryption and to better protect Intel’s intellectual property, Intel IT is deploying the Intel Solid-State Drive (Intel SSD) Professional Family (currently consisting of the Intel SSD Pro 1500 Series and the Intel SSD Pro 2500 Series), combined with McAfee Drive Encryption 7.1.
Our encryption journey began in 2009 with the deployment of Intel SSDs and software-based encryption. As technology matured, we moved to a more stable software-based encryption solution that was integrated with the already deployed McAfee ePolicy Orchestrator software—providing a “single pane of glass” view for all McAfee security products we were using. (The previous software-based encryption solution used a separate management system.) Later, we developed a custom hardware-based encryption management solution. These solutions provided incremental improvements for both users and IT employees.
Our current centrally managed hardware-based solution offers additional advantages:
• There is no noticeable impact on laptop performance.
• Encryption and decryption activation now takes just a few seconds, whereas software-based encryption took over an hour.
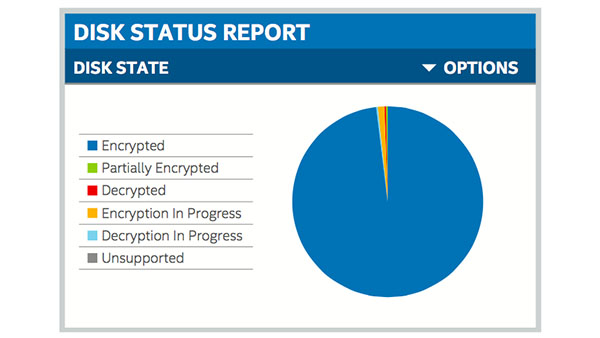
• Integration with McAfee ePolicy Orchestrator software enables us to track encryption compliance and generate encryption reports.
• The solution is easily scalable to accommodate growth in our PC fleet.
Our environment includes some older solid-state drives that still require software-based encryption. McAfee Drive Encryption provides the same user interface for both types of encryption and can automatically and transparently detect whether to use software-based or hardware-based encryption, depending on drive type.
Intel SSDs and McAfee Drive Encryption work in tandem to provide a more secure, higher-performing solution than either the latest encryption or SSD technology alone could.
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security

