Private Cloud PaaS – Accelerating Application Deployment
 |
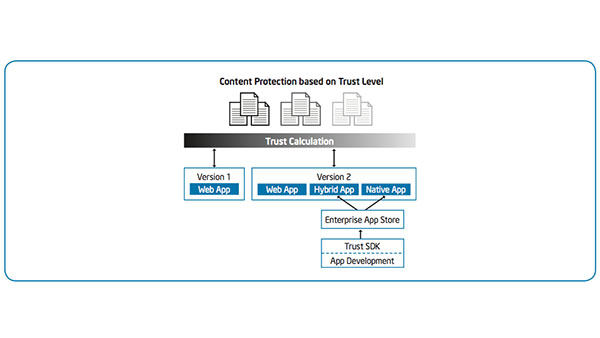
IT Best Practices: Intel IT is implementing platform as a service (PaaS) to accelerate custom application deployment and promote cloud-aware application design. Our traditional application deployment process is less-than-ideal, taking as much as 140 days to deploy a new application. [See the full post…] |
|
|