Measuring the Value of Information Security Investments
January 30th, 2012 |
Connected Social Media Syndication
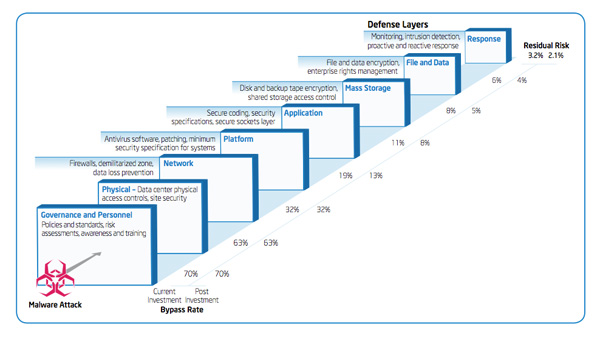
IT Best Practices: Intel IT finance created a new information security investment model which allows IT management, financial experts and security professionals to analyze and prioritize investments, based on risk mitigation against a variety of security threats. A key strength of the model is its ability to assess new and existing investments within the context of our IT environment, rather than in isolation.
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Information Technology, Intel, Intel IT, IT White Papers, IT@Intel

