Insider Threat Field Guide
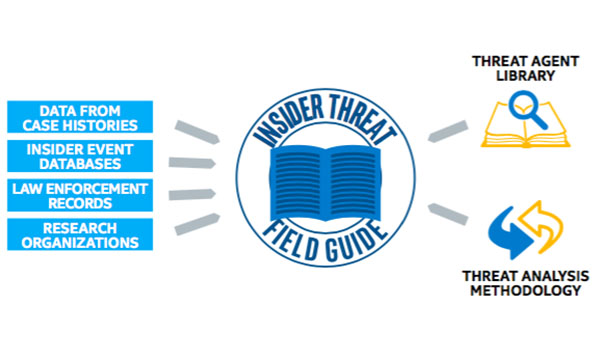
IT Best Practices: One of the most serious security challenges facing enterprises today is that of insider threat. However, many enterprises do not fully understand the scope of the problem and until recently, there has been a lack of tools to respond to this challenge.
Using the Threat Agent Library developed by Intel IT, study of published material, and discussions with other enterprises, we have created an Insider Threat Field Guide that identifies 60 most likely insider threat attack vectors. In particular, the guide does the following:
• Facilitates clear and consistent sharing of information, both internally and externally.
• Enables more effective security strategies and faster responses by risk managers, policymakers, auditors, and security specialists.
We believe enterprises can use our field guide to better understand insider threats and take steps to minimize the associated risks.
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Information Technology, Intel, Intel IT, IT White Papers, IT@Intel

