Insider Threat Field Guide
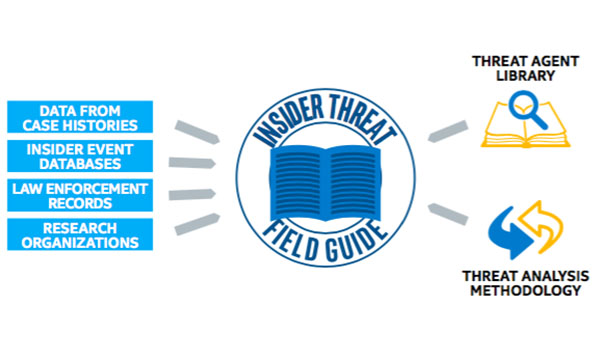 |
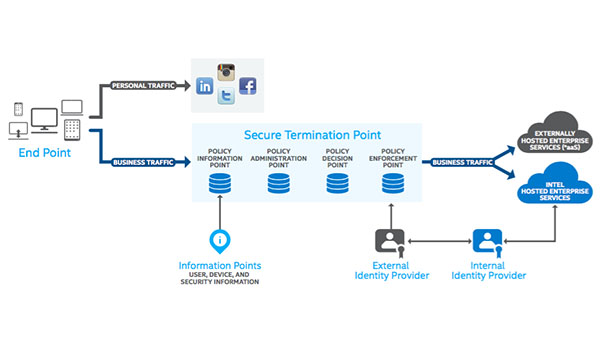
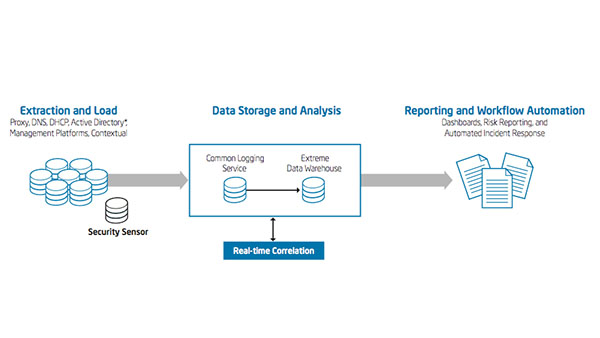
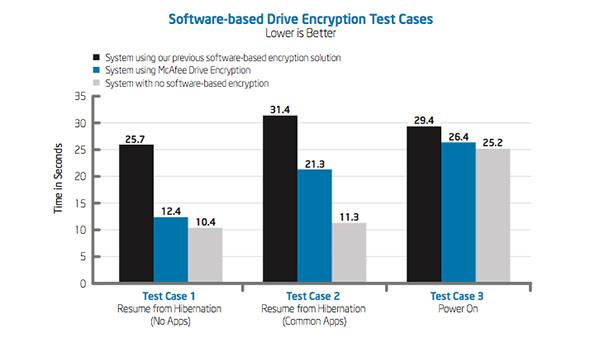
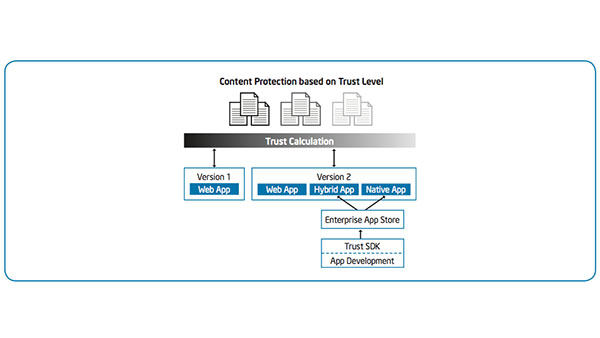
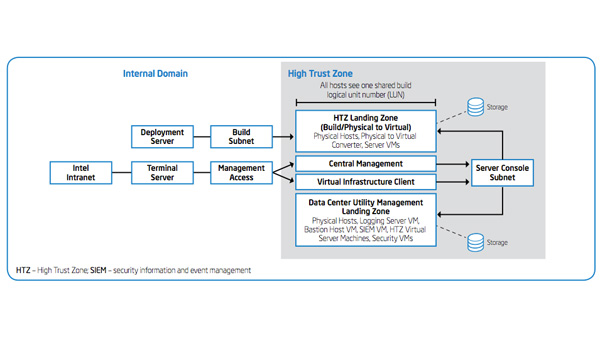
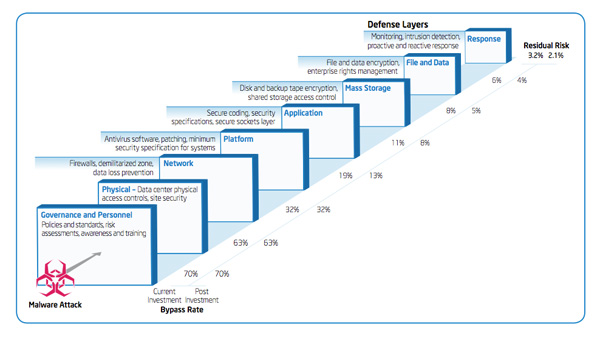
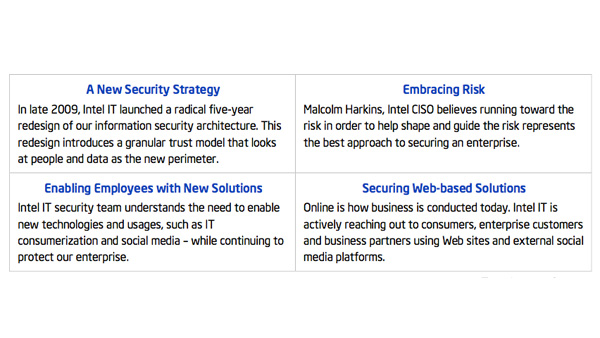
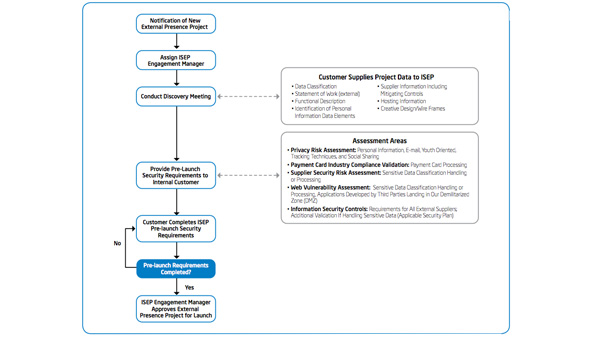
IT Best Practices: One of the most serious security challenges facing enterprises today is that of insider threat. However, many enterprises do not fully understand the scope of the problem and until recently, there has been a lack of tools [See the full post…] |
|
|