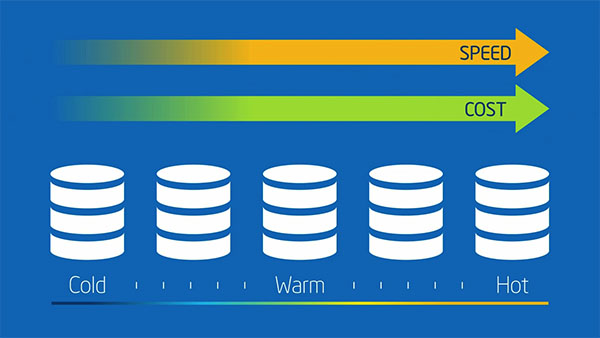
University Campus Suffolk: Empowering Next-Gen Game Designers
 |
Business Solutions for IT Managers: The Intel Xeon processor E5 family and Fujitsu CELSIUS M730 workstations bring professional-standard hardware to the Computer Games Design degree course at University Campus Suffolk. |
|
|