Boosting IaaS and PaaS Security in the Public Cloud
IT Best Practices: IT departments everywhere face what appears to be conflicting business needs: the need to take advantage of the agility and technology provided by the public cloud and the need to keep proprietary information secure.
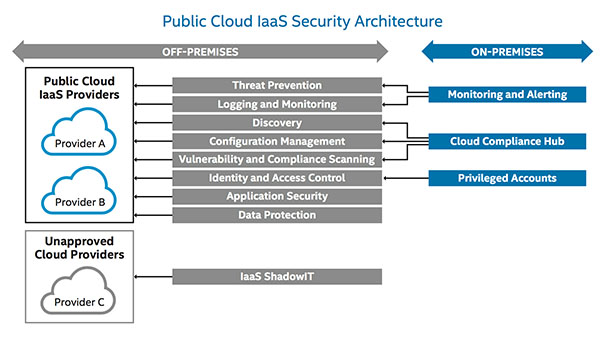
Recently, Intel IT has developed a public cloud infrastructure-as-a-service (IaaS) security strategy, which also encompasses platform-as-a-service (PaaS) security. This strategy, complemented by a comprehensive IaaS security architecture, enables Intel business units to use public cloud IaaS to accelerate innovation and time to market while cutting costs.
Successful public cloud usage involves more than just technology. We have adopted new tools, made substantial enhancements to relevant processes, and invested in people’s skill sets. We have found that we must regularly invest in developing our IT skills to securely enable Intel’s growing number of public cloud IaaS use cases.
Our long-term public cloud IaaS security strategy enables us to apply a compliance process not just to individual IaaS components but also to the entire cloud security configuration.
Other benefits include:
- Reduced cost through reuse of security tools and services
- More agile response to business needs
- Alignment between on-premises and public cloud IaaS security strategies and architectures
Key learnings pave the way for future work:
- Distributed accountability for IaaS security
- Effective discovery, vulnerability management, and compliance processes for IaaS use cases
- Strong identity lifecycle management process and data protection
- Choice of cloud-oriented solutions
- Cross-domain team building, combined with various skillsets
We continually assess and enhance security and privacy capabilities, processes, and people’s skills to protect Intel’s data and the data of our customers.
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Cloud Computing, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security

