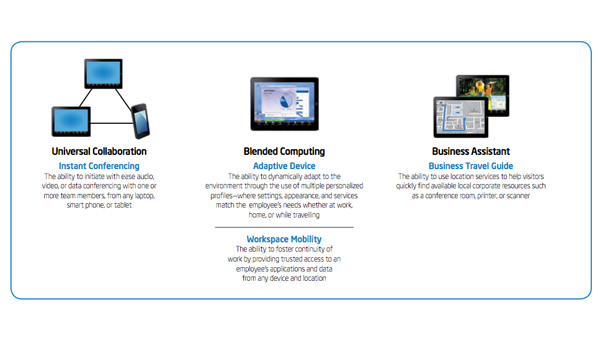
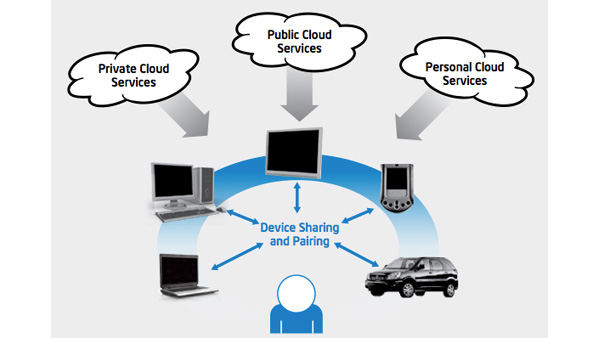
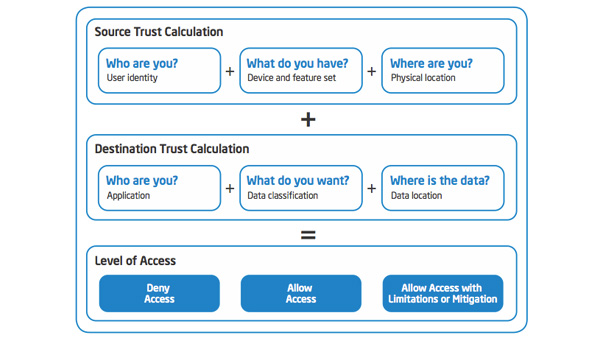
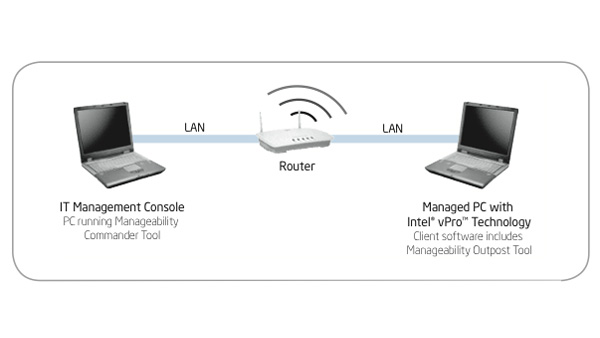
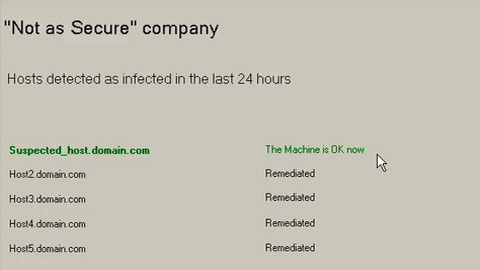
Why the Device Matters in a Cloud-centric World
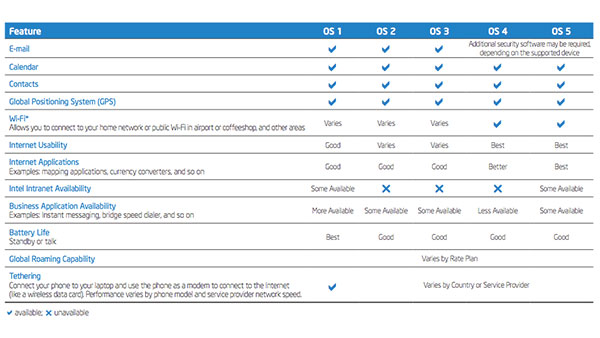 |
As services and data move to the cloud, Intel IT has found that the end–point device is not only retaining its relevancy, but is also becoming even more important. This belief runs contrary to the industry assumption that the abstraction [See the full post…] |
|
|