 |
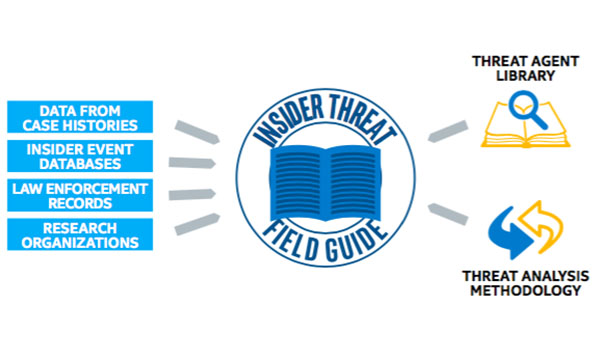
IT Best Practices: One of the most serious security challenges facing enterprises today is that of insider threat. However, many enterprises do not fully understand the scope of the problem and until recently, there has been a lack of [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Enterprise Security, information technology, insider event, insider risk, insider threat agent, Insider threat guide, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, IT@Intel, mitigating risk, pdf, threat agent library, Tim Casey
 |
Security risk assessments, security risk modeling, and protecting against security threats by maintaining a threat agent library — these and other programs form the basis for understanding threats to network security for Intel. In this video podcast, TIm Casey, senior [See the full post…] |
 Watch/download video Watch/download video
|
|
Categories: Connected Social Media, Corporate, Information Technology, Intel, Intel IT, IT@Intel Tags: Cyber Risk Management, cyber terrorism, hackers, information security, Intel, IntelSecurity, IT Information Security, Matthew Rosenquist, network security, Open Port, Security risk assessments, security risk modeling, security threats, threat agent library, threat agents, Tim Casey, war games
 |
“People are the ultimate threat,” says Tim Casey, a senior strategic analyst for information security at Intel. “People write the viruses, people throw the bombs.” In this interview with PodTech’s Jason Lopez, Casey says that security is all about being [See the full post…] |
 Listen/download audio Listen/download audio
|
|
Categories: Connected Social Media, Corporate, Information Technology, InfoWorld, Intel, Intel IT, Intel-OpenPort, IT@Intel Tags: Cyber Risk Management, datacenter, information security, Intel, IntelSecurity, IT Information Security, Jason Lopez, Tim Casey, viruses


