 |
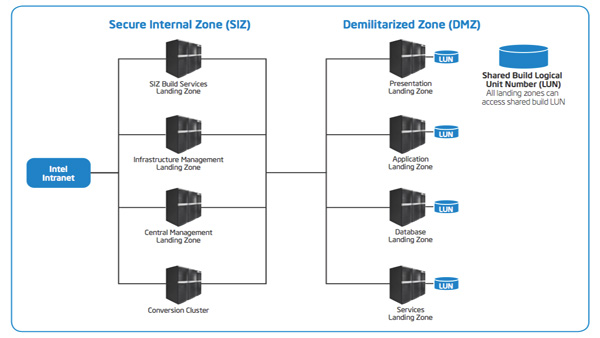
IT Best Practices: The purpose of this paper is to describe how Intel IT neutralized security risks that have allowed us to enable virtualization for the DMZ and SIZ thereby allowing Intel IT to expand the benefits of virtualization. [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Information Technology, Intel, Intel IT, IT White Papers, IT@Intel Tags: Cloud Security, Cloud Security Architecture, Data Center Solutions, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, Virtualization Security
 |
IT Best Practices: The purpose of this paper is to describe how Intel IT neutralized security risks that have allowed us to enable virtualization for the DMZ and SIZ thereby allowing Intel IT to expand the benefits of virtualization. [See the full post…] |
 Read/Download PDF Read/Download PDF
|
|
Categories: Corporate, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, virtualization Tags: Cloud Security, Cloud Security Architecture, Data Center Solutions, Intel, Intel IT, IT Best Practices, IT Business Value, IT Whitepaper, pdf, Virtualization Security


