IT Best Practices: Improving Data Protection with McAfee Drive Encryption
IT Best Practices:
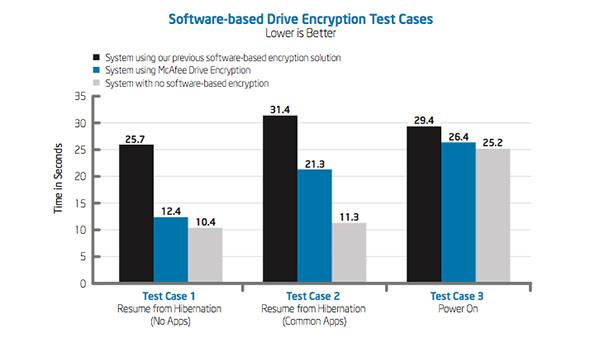
Intel IT is replacing our previous software-based encryption solution with McAfee Drive Encryption, an integral component of new McAfee security products such as McAfee Complete Data Protection – Advanced software. This high-performing, reliable solution provides integrated manageability, compliance reporting capabilities, and an improved user experience. McAfee Drive Encryption provides a hybrid agent that can automatically detect whether software- or hardware-based encryption is needed. This hybrid approach is an important aspect of encryption manageability for Intel IT because our environment includes an installed base of laptops with Intel Solid-State Drives (Intel SSDs) and non-Opal-compliant, self-encrypting drives (SEDs), which require software-based encryption. Our environment also includes Opal-compliant drives, such as the Intel SSD Pro 1500 Series, which support hardware-based encryption. We expect to complete the migration to McAfee Drive Encryption across Intel’s laptop fleet by mid-2014.
Hear more about this project Inside IT: McAfee Drive Encryption at Intel
Watch a video on supporting a hybrid environment of Opal-compliant Intel SSD Pro 1500 series drives plus self-encrypting drives which require software-based encryption, using McAfee Drive Encryption with McAfee ePolicy Orchestrator.
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Corporate, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security

