Improving Security and Mobility for Personally Owned Devices
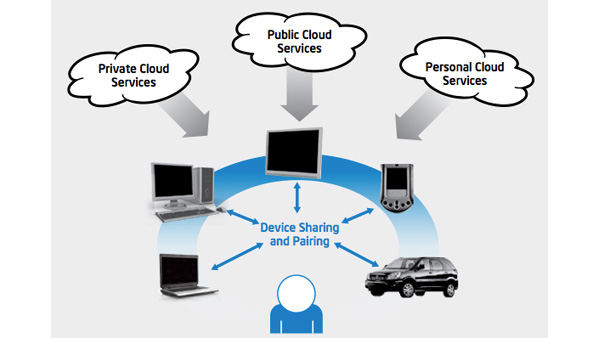
IT Best Practices: Intel IT has made significant progress in responding to the growing demand for use of personally owned devices, such as smart phones, tablets and PCs in the Intel work environment.
To support this initiative, we have developed an end-to-end security model, and are also enabling workspace mobility – a concept for providing trusted access to applications and data “workspaces” from any device with workspace mobility, so employees can enjoy a more consistent user experience across multiple devices.
The desire to bring personally owned devices to the workplace, classroom or other environment transcends industry and geographic boundaries. In this paper, we also explore some of the similarities between the classroom environment and enterprise environments that allow bring your own device (BYOD).
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Intel IT, IT White Papers, IT@Intel, Security

