IT Best Practices: Overcoming Security Challenges to Virtualize Internet-facing Applications
November 17th, 2011 |
Connected Social Media Syndication
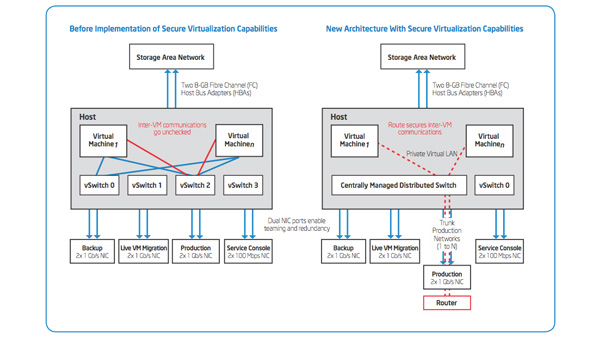
IT Best Practices: The purpose of this paper is to describe how Intel IT neutralized security risks that have allowed us to enable virtualization for the DMZ and SIZ thereby allowing Intel IT to expand the benefits of virtualization. Over time, we plan to further enhance our secure virtualization capabilities by taking advantage of hardware-assisted security with Intel TXT and Intel Advanced Encryption Standard New Instructions (AES-NI).
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Corporate, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, virtualization

