Intel IT Best Practices: Information Security should Protect and Enable
June 24th, 2011 |
Connected Social Media Syndication
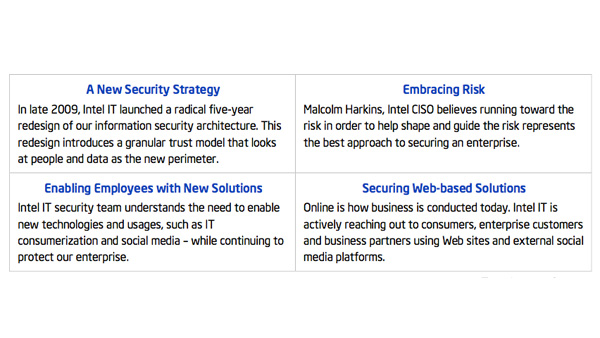
Intel IT Best Practices: At Intel IT we realized we needed to rethink how we approach enterprise security. We cannot continue to spend all our resources trying to block every threat. Our new approach takes into consideration that the role of enterprise security is to both protect and enable Intel’s business, including supporting new usage models like cloud computing, IT consumerization and social computing.
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Cloud Computing, Information Technology, Intel, Intel IT, IT White Papers, IT@Intel, Security

