Prioritizing Information Security Risks with Threat Agent Risk Assessment
October 12th, 2010 |
Connected Social Media Syndication
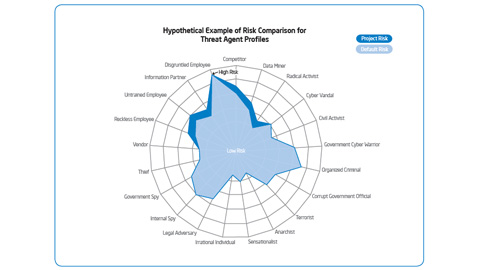
IT Business Value: Intel IT has developed a threat agent risk assessment (TARA) methodology that distills the immense number of possible information security attacks into a digest of only those exposures most likely to occur. This methodology identifies threat agents that are pursuing objectives which are reasonably attainable and could cause unsatisfactory losses to Intel.
For more information on Intel IT Best Practices, please visit intel.com/IT
Posted in:
Information Technology, Intel, Intel IT, IT White Papers, IT@Intel

